Infographics
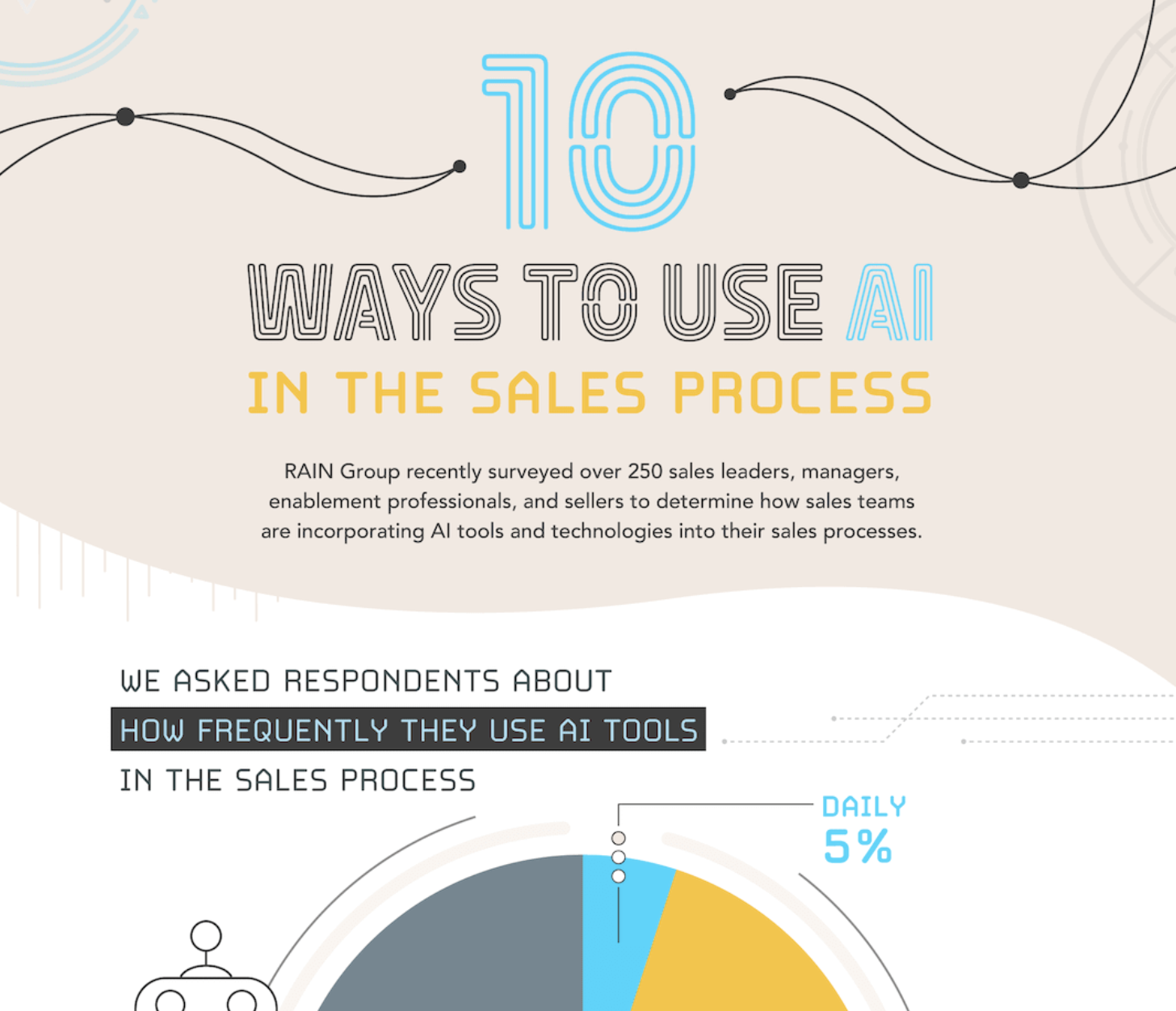
10 Ways To Use AI In The Sales Process
RAIN Group recently surveyed more than 250 sales leaders, managers, enablement professionals, and sellers to…
The Difference Between Micro- & Nano-Influencers
Recent research found that 86% of B2B organizations are using influencers to help build brand credibility,…
7 Steps To Mastering Social Media Management
Social media is essential to business growth, but the ever-evolving trends and user preferences make…
Harnessing LinkedIn’s Professional Network For Growth
LinkedIn can be an efficient marketing strategy to generate more leads and brand awareness— this…
How To Craft Evergreen Content
For content to be classified as evergreen, it needs to be continuously relevant and fresh…
B2B Marketing Benchmark: Spotlight On The Tech Industry
Despite budget challenges, marketers at B2B technology companies are optimistic about the future and excited…
Subdomain Vs. Subdirectory: What’s The Difference?
Both subdomains and subdirectories are important aspects of a website's architecture, and this infographic outlines the…
Data Never Sleeps 11.0
Over the past decade,data experience platform Domo tracked the world's data usage, revealing remarkable increases…
How AI & The Metaverse Will Impact The Datasphere
The datasphere—the infrastructure that stores and processes our data—is critical to many ofthe advanced technologies…
Content Marketing Checklist
Content rules all aspects of B2B marketing, meaning it's important that marketers remain up todate…
5 Steps To Setting Up An Organic Marketing Strategy
Organic marketing is key to generating unpaid content visits, and this infographic outlines the five…
6 Social Media Marketing Predictions For 2024
As companies start focusing on their 2024 goals, they're making sure they're innovating their social…