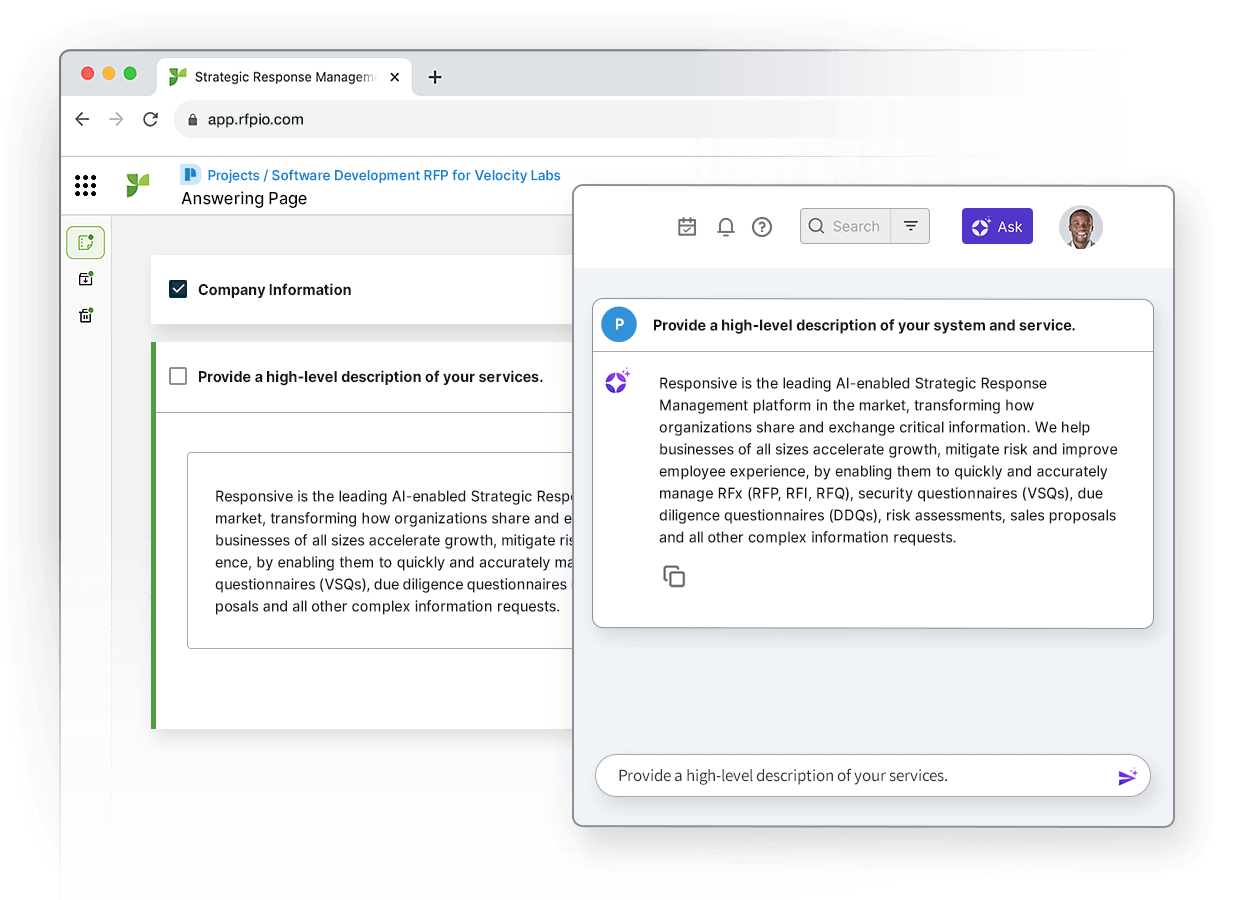
Responsive — (formerly RFPIO) — provides strategic response management (SRM) software to help organizations share and exchange critical information. The AI-powered Responsive Platform is purpose-built to manage responses at scale with the goal of empowering companies across the world to accelerate growth, mitigate risk and improve employee experiences.
Solution Overview
According to the company, Responsive is the industry’s first AI-powered SRM platform that enables organizations to seamlessly collaborate and confidently respond to RFPs, bids, security questionnaires, sustainability assessments and other information requests so they can win more deals while mitigating business risk and improving the employee experience.
Back-Of-The-Box Details
The Responsive Platform, which is designed to centralize an organization’s most current and compelling, customer-facing information, is engineered around five core tenants:
- Content management to ensure a single source of accurate, trusted content;
- Project management to establish tasks and automate workflows using AI;
- Collaboration to streamline input, iterations and permissions based on role;
- Content accessibility that allows users to access information directly from the apps they’re in every day; and
- Business intelligence to track revenue, win rates and emerging trends and opportunities.
Who It’s For
Nearly 2,000 customers have standardized on Responsive to respond to RFPs, RFIs, DDQs, ESGs, security questionnaires, ad hoc information requests and more.
What Makes It Special
According to the company, part of Responsive’s success has been its deep commitment to rapid, customer-driven innovation, extensive incorporation of AI into its solutions from day one and focus on delivering value to customers.
Contact
Do you have a solution you’d like to spotlight? Fill out our submission form for editorial consideration!