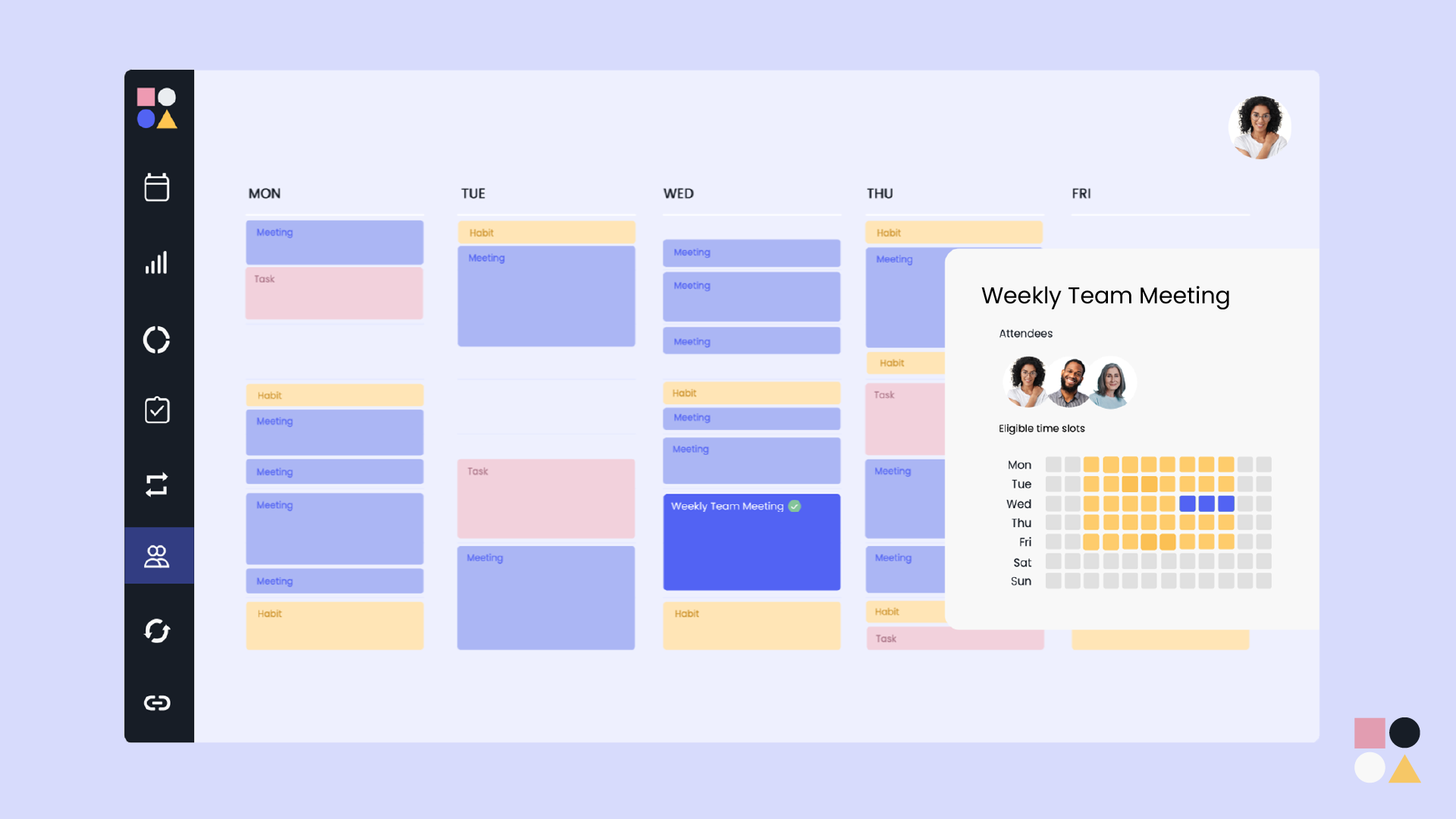
Reclaim.ai is an AI calendar app designed to automatically schedule meetings, tasks, habits and breaks around a user’s existing calendar. The company also issues quarterly productivity trend reports on key industry topics to highlight how teams are optimizing their workweeks in the modern workplace.
Solution Overview
The company’s Smart Meetings solution seeks to automate meeting scheduling across all attendees’ calendars using AI and machine learning to automatically considering everyone’s time zones, availability and priorities.
Back-Of-The-Box Details
Key features of Smart Meetings include:
- AI auto-scheduling, rescheduling and flexibility to adapt to calendar changes;
- Machine learning to detect frequently skipped meetings, track why they were skipped and raise their scheduling priority;
- Native conference room integrations to add the right meeting room to an agenda; and
- Additional integrations with other platforms that help manage agendas, status reporting or meeting rooms.
Who It’s For
Reclaim.ai seeks to help individuals, teams and enterprises automatically align their time to their top priorities and solve complex scheduling challenges.
What Makes It Special
According to the company, Smart Meetings is the first solution to deliver true intelligence for meeting scheduling by using priorities and context to know when meetings can be adjusted, negotiated or rescheduled, and when they can’t.
Contact
Do you have a solution you’d like to spotlight? Fill out our submission form for editorial consideration!